Mobile apps have assimilated into all daily lives in today’s fast-paced digital world. Mobile apps provide accessibility and convenience unlike anything else, from banking and shopping to socializing and entertainment. The growing reliance on mobile apps also raises thoughts about security and privacy. To safeguard sensitive user data, it is essential to have strong security measures in place, given the increase in cyber threats and data breaches. Hashing algorithms are one such measure that significantly contributes to improving the security of mobile apps.
Knowledge of Hashing Algorithms
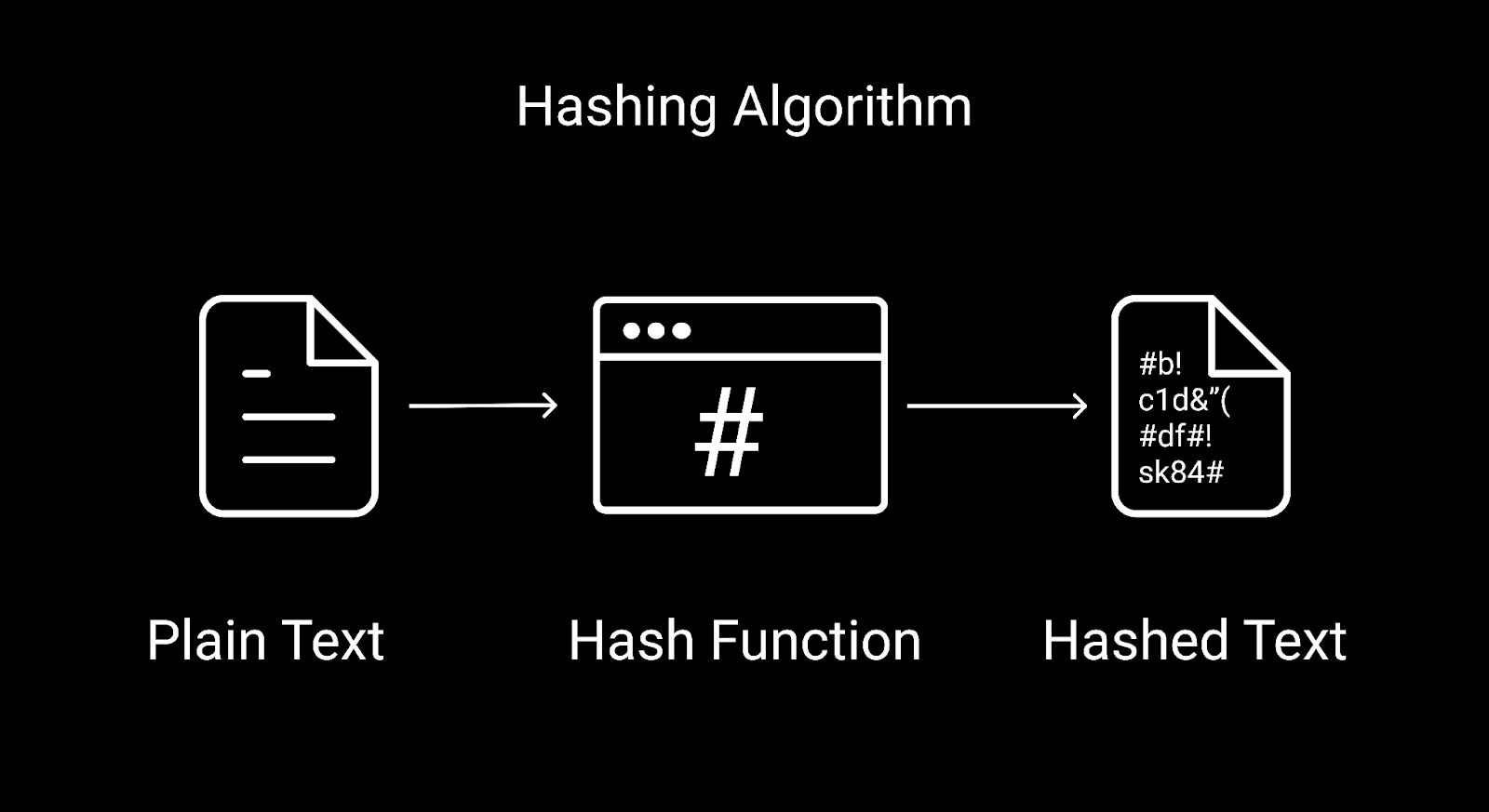
How do you define a hashing algorithm?:
A hashing algorithm is a mathematical formula that, given specific input data, generates a fixed-length character string known as a hash value or digest. Since hashing techniques are one-way functions, it is computationally impossible to reconstruct the original input from the hash value. This is a significant characteristic of hashing algorithms. Because of this characteristic, they are perfect for safeguarding data and ensuring its integrity.
Mobile App Security Using Hashing Algorithms
These algorithms can be used in a variety of ways by mobile app developers to improve security:
Password Storage: Plaintext password storage for user accounts is a serious security concern. Instead, programmers can hash passwords. The software hashes and compares the user’s password to the previously stored hash value. This will prevent the original passwords from being recovered, even if an attacker acquires access to the password database.
Data Integrity: Data integrity for the mobile app can be guaranteed via hashing techniques. Developers can ensure that sensitive data, such as user profiles or transaction details, has not been tampered with by hashing it. It shows data modification and warns the app of potential security breaches if the hash values don’t match.
Digital Signatures: For the security of mobile apps, hashing techniques are essential for implementing digital signatures. A mathematical formula known as a digital signature confirms the legitimacy and consistency of digital messages and documents. The recipient can verify the signature by computing a hash of the message, encrypting it using the sender’s private key, and decrypting it with the sender’s public key. This guarantees that the message wasn’t altered while it was in transit.
Mobile Apps that Use Hashing Algorithms
Selecting the Correct Algorithm:
Developers must choose an appropriate algorithm based on security, efficiency, and compatibility when using these algorithms in mobile apps. It’s crucial to remember that outdated algorithms have flaws and are no longer suggested for secure hashing.
Adding Salt for More Security:
Developers can use salting to reduce the danger of brute-force assaults and rainbow table attacks.Before hashing, a process known as salting includes adding a random value, or salt, to the input. Because each user’s salt is distinct, their hash values will differ even if two users have the same password. This increases security and makes it more difficult for attackers to guess passwords.
Keeping Hashing Algorithms Up To Date:
The methods used by attackers change along with technological advancements. Keeping up with the most recent developments in these algorithms is crucial. Developers should frequently assess the security precautions in their software and, if necessary, consider updating to newer, more secure algorithms.
Continuous Threat Detection and Monitoring
Examining App Activity:
Implementing hashing methods during development is only one aspect of protecting mobile apps. It’s crucial to continuously monitor app behavior to spot and address any potential security issues. Developers can spot suspicious activity and take proactive steps to reduce risks by analyzing app usage trends, network traffic, and user interactions.
Systems for detecting intrusions:
IDSs (intrusion detection systems) are crucial for keeping track of mobile app security. These systems use complex algorithms to analyze network traffic and find any indications of harmful or intrusive activities. IDS can produce alerts for rapid action when it notices patterns suggestive of attacks, such as attempts at data exfiltration or unauthorized access.
Instantaneous Threat Information
Mobile apps that use real-time threat intelligence services can add an extra layer of security. These services continuously gather and examine data about potential threats and weaknesses. Mobile apps can use this intelligence to proactively identify and address potential security concerns, protecting user data from the most recent attack vectors.
User Training and Secure Procedures
Secure Password Guidelines:
Weak passwords are frequently among the mobile apps’ most significant security gaps. App security can be significantly improved by informing users of the value of solid passwords and enforcing strict password regulations. Encourage users to make complicated, one-of-a-kind passwords and instruct them on best practices, such as combining letters, numbers, and symbols.
The second factor of authentication:
Two-factor authentication (2FA) is a security measure that may be added to mobile apps. Even if an attacker succeeds in obtaining the user’s password, they would still need other credentials to get access by asking users to give a second form of verification, such as a unique code sent to their registered email address or a biometric scan.
Recurrent Updates and Patch Administration:
Mobile app developers should prioritize regular updates and patch management to fix known vulnerabilities quickly. This entails changing the underlying libraries and frameworks in addition to the coding of the application. The app’s continued protection against the most recent threats and vulnerabilities depends on the prompt application of security patches.
Leveraging these algorithms is a critical step in strengthening protection in the constantly changing mobile app security world. Developers can safeguard user data, guarantee data integrity, and defend against numerous attacks by employing robust algorithms. However, protecting mobile apps involves a comprehensive approach that includes ongoing surveillance, threat identification, user amplification, and adherence to safety procedures.
Developers may strengthen the security posture of their applications by integrating intrusion detection systems, utilizing real-time threat intelligence, teaching users about password security, adopting two-factor authentication, and routinely upgrading and patching mobile apps.
Conclusion:
Mobile app security is crucial in a world that is becoming more connected. A practical method for strengthening user data safety and guaranteeing the integrity of mobile applications is these algorithms.
Appsealing App developers can significantly lower the risk of data breaches and unauthorized access by adopting appropriate algorithms and adhering to standard practices like salting and regular updates. Staying vigilant and prioritizing strong security measures will be essential in protecting user privacy and preserving trust in mobile app ecosystems as the landscape of mobile apps continues to change.
Read More: